TL;DR Blockfence recently discovered a rug pull scam carried out through the Telegram group “NoLiquids”, where the scammers promoted fake tokens that included hidden malicious functions designed to deceive investors.
This investigation unveils the operation of the group, the technical aspects of the malicious tokens, and finally, the trace of around 300 ETH of stolen funds that were finally deposited into Biget and Bybit.
Inside the scammers’ operation
This group has nearly 43K members. Our investigation of four fake tokens shows that approximately 1K users may have fallen into this scam. However, considering this group has been active since mid-2019, we believe the number of victims may be significantly higher.
The Telegram group can be accessed through this URL: https://t.me/NoLiquids
Be VERY careful and only use it for research purposes.
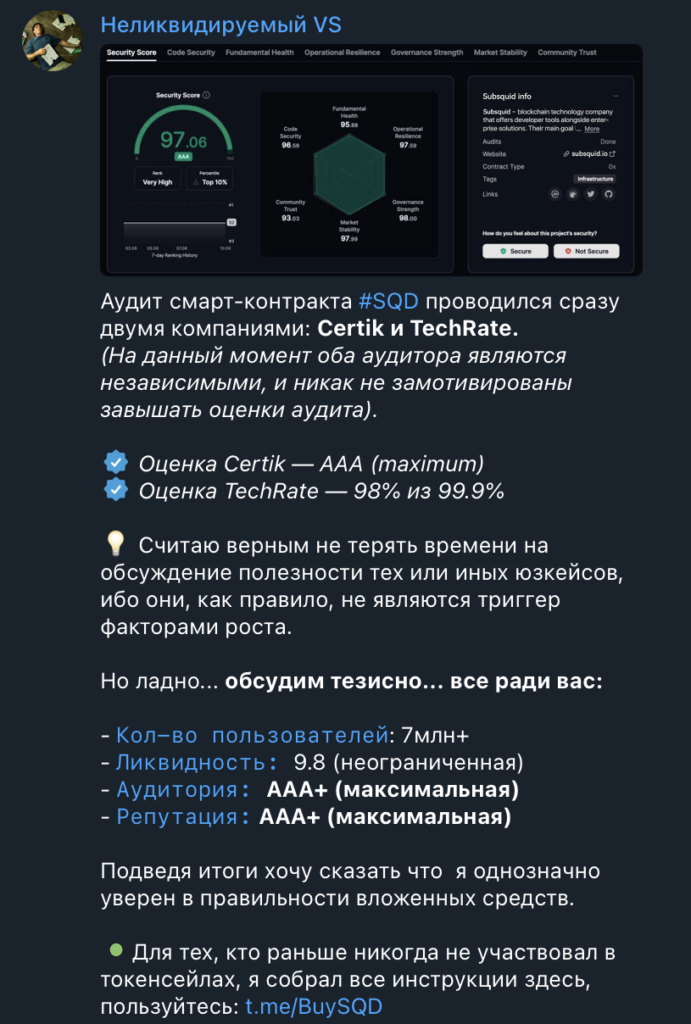
This Telegram group pretended to audit the SQD smart contract using legitimate companies like Certik and TechRate. The group sent out a fraudulent message stating this in Russian.
We have translated the message into English:
Two companies carried out the audit of the #SQD smart contract at once: Certik and TechRate.
(Currently, both auditors are independent and are not motivated to inflate audit estimates).✅ Certik rating – AAA (maximum)
✅ TechRate – 98% out of 99.9%💡 I think it’s best not to waste time discussing the usefulness of certain use cases because they, as a rule, do not trigger factors for growth.
But okay… let’s discuss it briefly… all for your sake:
– Number of users: 7 million+
– Liquidity: 9.8 (unlimited)
– Audience: AAA+ (maximum)
– Reputation: AAA+ (maximum)To sum up, I want to say that I am definitely confident in the correctness of the investment.
🟢For those who have never participated in token sales before, I have collected all the information
Another message from this Telegram group, which we can see here translated into English, instructs victims on purchasing fake tokens using direct links.
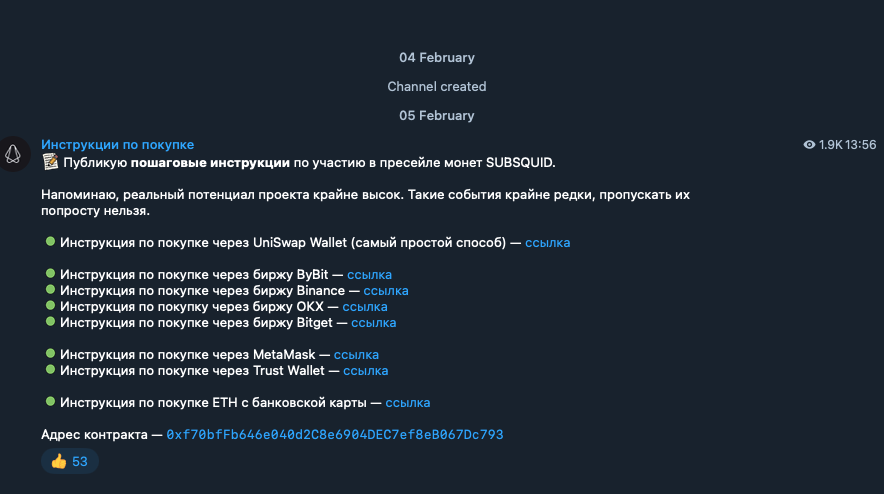

Example For how The scammers instruct the victims to make a purchase using Metamask (check with precaution, research purposes only)
https://telegra.ph/Instrukciya-po-pokupke-SQD-02-04-4
Analyzing the fake tokens’ code
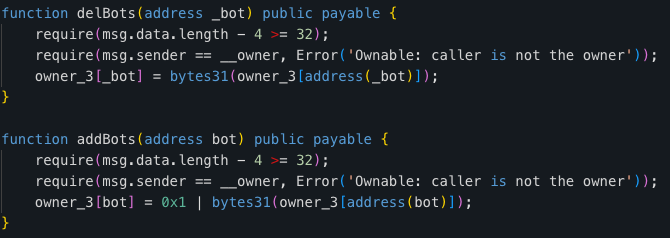
We have discovered that the smart contract code used by all four fake tokens is highly similar. After comparing two smart contract codes, we found that both code sets have several key similarities in their potential honeypot indicators. Let’s review them together.
Token 1 – SQD: 0xf70bfFb646e040d2C8e6904DEC7ef8eB067Dc793
https://etherscan.io/token/0xf70bffb646e040d2c8e6904dec7ef8eb067dc793
Token 2 – DUO: 0xa17e4bbc99f92e8996bb594a4c41aa2ac25923c3
https://etherscan.io/address/0xa17e4bbc99f92e8996bb594a4c41aa2ac25923c3
These similarities include:
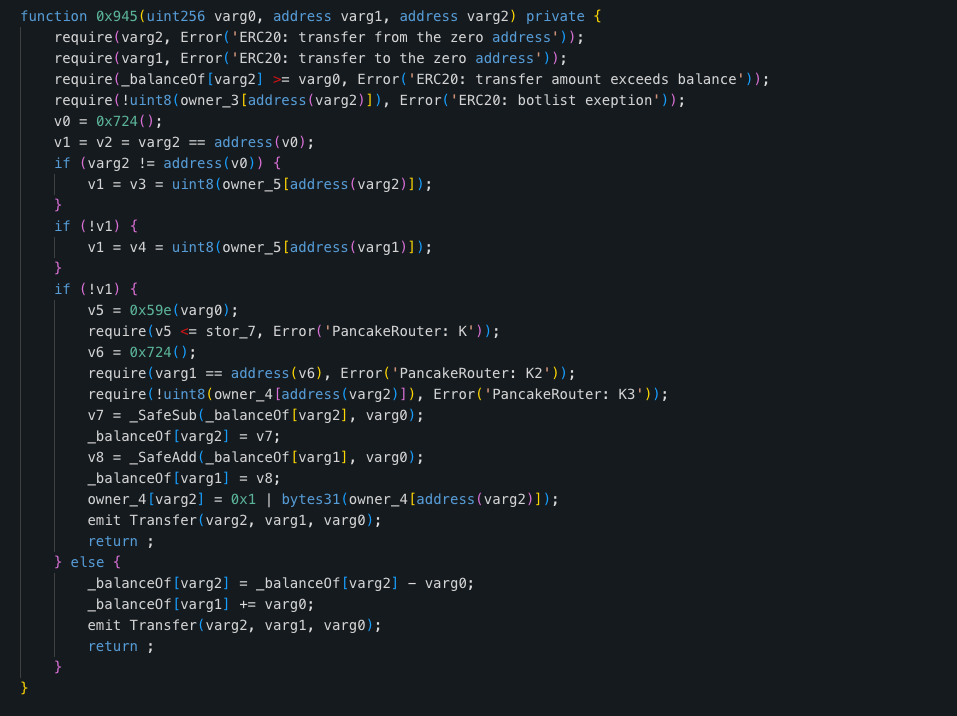
1 – Bot Management Functions: Both code snippets have unusual functions, such as addBots and delBots, which can blacklist or restrict specific addresses. These functions are commonly used in honeypot contracts.
2 – Complex Transfer Logic: Both contracts contain complex logic within their transfer functions. The transfer function (0x945) contains intricate logic that checks against multiple mappings (owner_3, owner_4, owner_5).
This complexity could be a warning sign as it may be used to trap user funds under specific conditions. For example, it may restrict transfers to or from a Uniswap pool or based on fee exclusion.
3 – Direct Manipulation of Allowances and Balances: Both contracts have functions that allow direct manipulation of allowances and balances. This is not typical for standard ERC-20 tokens and could potentially be used for malicious control over user funds.
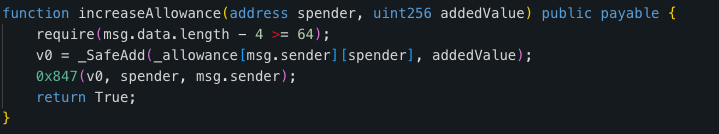
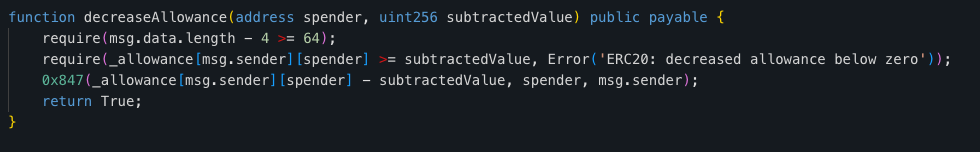
Our investigation uncovered three more fraudulent tokens besides the fake SQD token. All three followed the same pattern and, unfortunately, resulted in a rug pull.
This section will explain how we traced the victim’s funds to → exchange deposit.
During our investigation, we used the MetaSleuth tracing tool from BlockSec. The tool has a user-friendly interface and clearly visualizes the interactions between addresses in different chains.
You can check our full investigation here.
Tracing the stolen funds
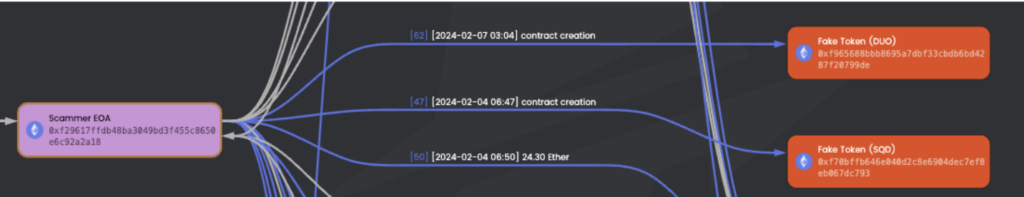
1 – The Trace of the victim’s funds began from this address: 0xf70bffb646e040d2c8e6904dec7ef8eb067dc793 (SQD Fake Token Contract) that was posted in the Telegram group channel.
As you can see, the scammer created two fake token contracts. Both use real project names, and one hasn’t yet released its token. Subsquid is one of them.
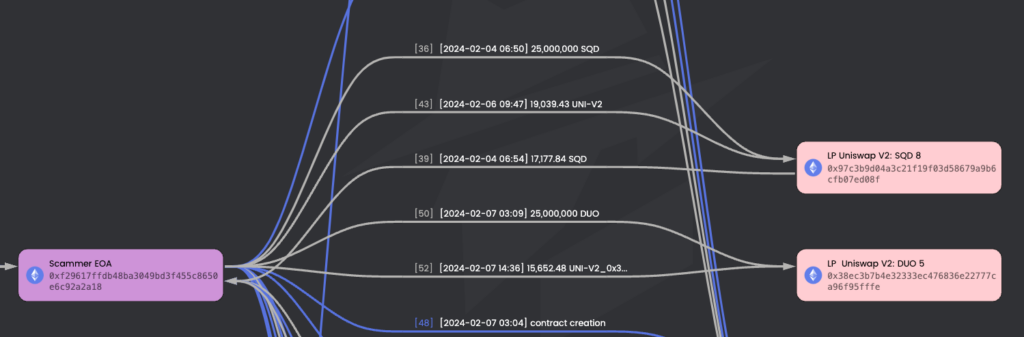
2 – The scammer created liquidity pools in Uniswap, added liquidity for both tokens and received the LP tokens for each.
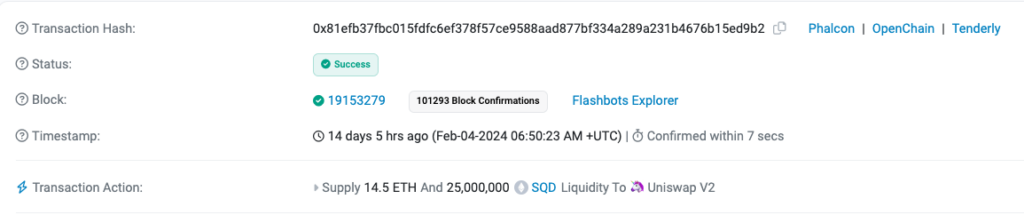
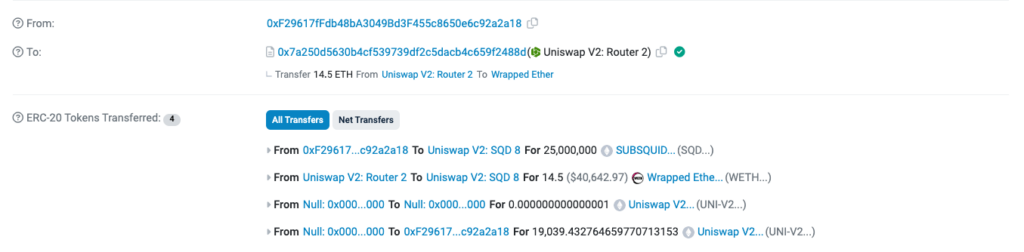
3 – The scammer added 14.5 ETH and 25M of SQD tokens. The full transaction details are in this Etherscan link.
4 – Users in the Telegram group begin purchasing tokens without realizing that they cannot sell them and become trapped. Here, we see an example of users sending WETH in exchange for fake tokens.
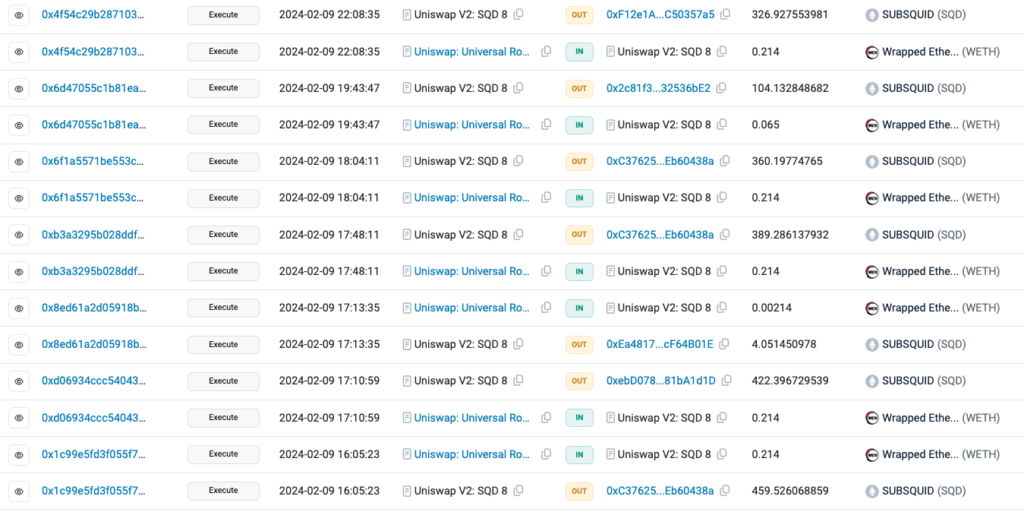
5. The scammer utilizes multiple transactions to remove liquidity from those pools. In this link, you can find all the execution transactions of the four fake tokens > Spreadsheet with all transactions.
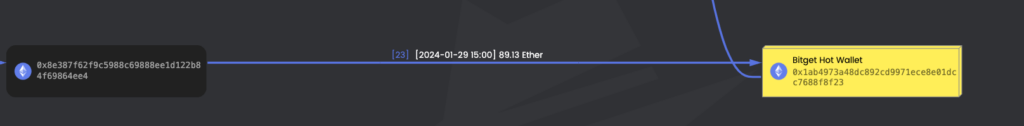
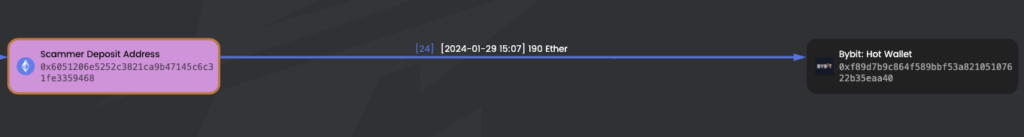
6 – After removing liquidity from all four tokens and executing the rug pulls, the scammer swiftly transferred the funds to accounts in exchanges Bitget and Bybit.
– Bitget address: 0x8e387f62f9c5988c69888ee1d122b84f69864ee4
– Bybit address: 0x6051206e5252c3821ca9b47145c6c31fe3359468
Please be aware that even today, there are ongoing attempts to deceive people with fake links and fraudulent images related to the Pixel Token from this Telegram Group.
As of today, these attempts are still active, even though the Pixel Token was listed some weeks ago on the market. It is essential to be cautious and suspicious of such links or images and to conduct research before trusting anyone or anything related to the Pixel Token.
We hope you enjoyed our research.
If you got any idea or detail you wanna add or correct, you can contact our researchers:
– Eyal Mor: Linkedin
– Pablo Sabbatella: Twitter – Linkedin