Designed for beginners and experienced alike, this article will serve as your guide to understanding the intricate world of private keys, delving into their definitions, mechanics, and best practices for secure usage.
However, to truly grasp the concept of private keys, we must first embark on a broader exploration of cryptographic systems, starting with the simpler symmetric cryptography and gradually unfolding the complexities of asymmetric cryptography.
Understanding Symmetric and Asymmetric Cryptography
What is Symmetric Cryptography
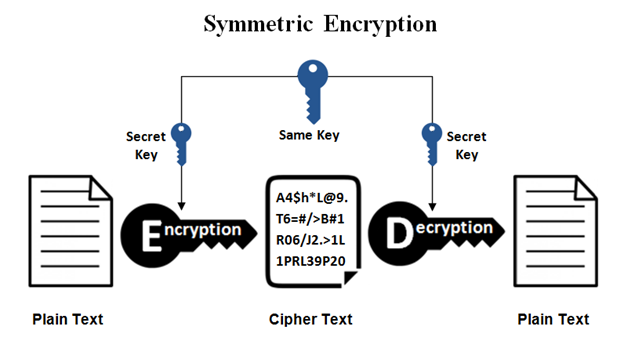
Symmetric cryptography was the old model used for encrypting information. Imagine Alice and Bob want to send encrypted messages to each other so that nobody can know what they are talking about if the message gets interfered with.
To do this, they both share a secret key (which can be a secret word or a password) and from there on, all messages that they send are encrypted (obfuscated) with that password, which is also used to decrypt (open) that message. The problem with such a mechanism is that we need Anna and Bob to get together to share that password initially or to have a secure channel to do so (less common).
What is Asymmetric Cryptography
In 1976, Diffie and Hellman introduced the concept of public key encryption, also known as asymmetric cryptography, to solve this problem. According to this mechanism, each side has a pair of keys: one private key and one public key.
The private key, as its name states, must be kept private and will be used for encrypting a message or signing transactions by the user.
On the other hand, the public key is published by the user and will be used by other users to verify that a message signed with a specific signature is valid (that the user signed it). A public key can also be used to encrypt a message that we want to be opened only by someone specific. So, if Alice wants to send an encrypted message to Bob, she will encrypt the message with her private key and Bob’s public key. Then Bob will be able to open (decrypt) the message with his private key and verify that the message was written by Alice using her public key.
Public Key Cryptography Applied to Web3
As you may already have noticed, blockchain security is based on asymmetric cryptography, also known as Public-key cryptography. We are using it to sign transactions with private keys and to verify them with their corresponding public keys.
Public and private keys are just strings of alphanumeric characters.
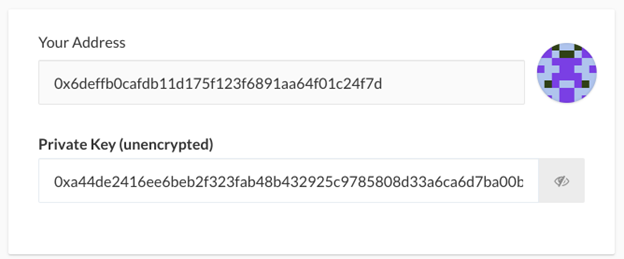
Each address, for example, 0xd8dA6BF26964aF9D7eEd9e03E53415D37aA96045, has both a public key and a private key.
Private keys look like this: c99565e6b48300be9ececf08111eb900efb206d0549de67f832feffa5ceaed1a, and it must be kept confidential because if you lose it or it gets stolen, you will lose access to your funds.
But to operate and transact simply, the ecosystem developed dedicated crypto wallets. Many think that wallets store cryptocurrencies, but that’s not true. Wallets hold the private keys, and by doing so, they allow sending transactions to the blockchain signed with these keys so that nodes can verify that the transaction comes from the actual owner of those assets.
Crypto Wallet: Hot, Cold and Warm
Regarding how to store private keys, we have three categories: hot, cold, and warm wallets. Hot wallets create and store private keys in devices that are connected to the internet. Cold wallets generate and store private keys in devices that do not have internet access, making them far more secure. Warm wallets, such as Muun Wallet, are in between hot and cold: they are a multisig of 2 keys, one of them is stored in the user’s device and the other in Muun’s server. Whenever a transaction is sent, Muun verifies that the transaction comes from the device where the wallet was originally installed. In that case, they will also sign with their second key, and the transaction will be broadcast to the Bitcoin blockchain (Muun does not support EVM networks yet). Today, we will focus on the first group (hot wallets) and how to use them safely.
How to Configure and Backup Your Private Key
When configuring a wallet for the first time, you are given 12 or 24 words to be stored safely; these words are called a seed phrase or secret recovery phase.
Hot wallets like Metamask usually use 12-word seed phrases, while hardware wallets like Ledger can also use 24 words.
This sequence of words should be saved securely and in order, as it lets your wallet recreate the private key and will be your backup in case your device breaks or the wallet installation gets corrupt.
Why do we back up seed phrases instead of private keys?
Because it’s easier to write down 12 words than a long string of nonsense characters where you may confuse characters, such as a 0 for an O or an l for an I.
Something interesting about seed phrases is that, in fact, each one of these words you are writing represents a number, so in case you consider yourself an advanced user, you could save the number instead of the word (not recommended for non-experienced users). You can check the whole BIP39 list here.
Where to Safely Store Your Private Key?
It’s crucial to store this seed phrase securely. So, what do we mean by that? Never send it by email, or social messaging, do not take a photo or save it on your PC, mobile device, or password manager (there have been multiple hacks due to storing them in this kind of app).
To sum it up, seed phrases should not be saved digitally. So, just write them down on two pieces of paper and store them in different secure locations, like your house, your bank’s safe, or your parent’s house. Remember that from a security point of view, it’s important to have both confidentiality (only authorized people can access it, so store it in a secret place) and Availability (avoid losing it yourself; that’s why it’s recommended to have two copies of it, also in case of physical damage like fire).
Another advice would be to add the order number that corresponds to each of the words, as some people order horizontally and some vertically.
There have been many cases of people who passed away, and all of their funds were lost since relatives didn’t have access to private keys. So it’s important to inform someone you trust how you have stored these keys in case something happens to you.
One Seed Phrase – Many Public Addresses
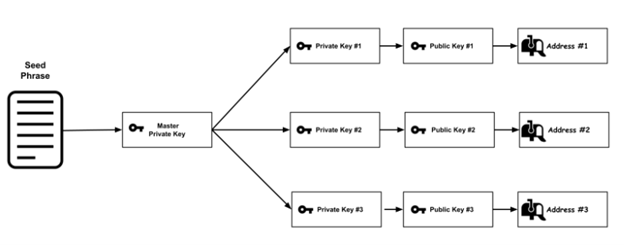
So, we have a seed phrase, which is used to generate the master private key using a hierarchical deterministic (HD) key generation algorithm such as BIP32. With that master private key, we will be able to derive N private keys, each private key is a 256-bit number represented in hexadecimal. All these private keys can be used to generate their corresponding public key.
Then, each public key is hashed using the Keccack-256 algorithm. From this 32-byte result, we take only the last 20 bytes (by removing the first 12 bytes) and add the 0x prefix; there, we have our Ethereum address.
If you have wondered, that’s why you can have many accounts under the exact seed phrase.
You can see an example of this in Metamask, which allows you to create multiple sub-accounts, each corresponding to a new address. This gives you more privacy, as even when you control all of these subaccounts or addresses, there’s no way for others to know they are related (unless you send transactions between them, obviously).
The Different Types of Attacks to Steal Your Private Keys
As we stated in the beginning, to sign transactions, hot wallets like Metamask or Rabby need to save your private key in your device (computer or mobile). This is usually stored inside a keystore file, which is a file that is encrypted with the wallet’s password you configured by the wallet. If that keystore file is stolen, attackers might be able to crack its password; that’s why it’s essential to set a very strong one.
So, cybercriminals are after your private keys, with which they will be able to steal your funds and assets. And they have many techniques to achieve this: we will understand them and explain how to protect ourselves from each one of these threats.
Malware
The most common nowadays is malware (what we used to call viruses or worms), which mostly comes after running a malicious file downloaded from torrent or pirate sites or downloads from phishing websites.
The malware will search your computer for installed wallets, extract the keystore files from them, log your password using a keylogger (a software that logs every key you press on your keyboard), and send valuable information to the attackers. It will also look for files with names or contents related to crypto, passwords, and seed phrases like bitcoin.txt, passwords.doc, and seedphrase.xls.
How do we avoid this attack? NEVER download cracked software and install as few applications as possible: only the ones that you really use and that come from a trusted source. Never run files you’re unsure about (even if it was sent from one of your contacts).
Social Engineering
Social engineering is the art of using deception in order to manipulate people into divulging confidential information.
This attack comes in many ways, and the most common is someone pretending to be on behalf of your wallet’s support team and asking you for your seed phrase (you may have seen this very often on Twitter with fake Metamask publications and replies). This may seem basic to most of us, but let’s repeat it: only a robber will ask you for your seed phrase. Metamask will never ask you for your seed phrase or private keys. NEVER share it with anyone. And if you are in doubt, the answer is always – NO!
Malicious Browser Extensions
There are a lot of unverified and harmful Chrome extensions that will be able to steal information from other extensions (such as private keys) from the websites you visit and even make you think you are visiting an official website while the extension has sent you to a phishing website.
How to avoid it? Always double-check that you’re installing the correct extension and not a fake one – check the number of downloads and reviews, and also look for the checkmark sign. In addition, uninstall any extensions you don’t use regularly and those you don’t trust its source. Having millions of downloads is not enough: there are many cases of malware in widely adopted extensions. You must also keep them updated. There’s a way to force auto-update in Google Chrome: Settings > Extensions > Developer mode > Update.
Browser Profiles: Have More Than One
In Cybersecurity, it’s common to talk about compartmentalization, that is, not having all the information and resources stored together, avoiding a SPOF (single point of failure), so if we have a security incident, not all the data gets stolen.
So, it’s recommended to compartmentalize your browser: create different Chrome profiles for you: one for crypto, one for work, and another for personal stuff. This way, if an infected extension is installed in your personal profile, it won’t affect your professional and crypto profiles. It also allows you to have separate bookmarks, saved passwords, and cookies, making it comfortable to work.
Phishing
Phishing is the art of tricking victims into revealing private information or installing malware by masquerading as a trustworthy entity. Their goal is to make you think you are entering a website when you are entering a malicious website impersonating the original website, that it intends to steal your data. This includes:
- Twitter posts, replies, or ads trick you into visiting their websites or dapps that will make you claim an airdrop.
- Discord and Telegram links impersonating communities or celebs.
- Emails from services that are known to you (exchanges, fintech, banks, or dapps)
- Google ads: you search for an exchange, and the first result you see is not that exchange but a paid ad with the same name; most likely, it will redirect you to a malicious website.
Lots of platforms’ client databases have been stolen, so that’s how criminals know you use that service.
If you are being targeted, phishing attempts will be far more sophisticated: they will come from people and entities you know, with information that is not public. Also, many phishing attempts come from verified and real accounts that have been hacked, so you have to be extra careful with official announcements that come from nowhere, especially on Twitter, Discord, and Telegram. Remember – there is no free lunch.
How to avoid it? Bookmark key websites such as dapps, exchanges, and blockchain tools so that you can access them from your navbar directly. Never google them or click on links from social media, emails, telegram, discord, etc. But in case some of these measures fail, we need a safety barrier: use a tool to detect phishing and scam websites and smart contracts, like Blockfence Extension or Metamask Snap.
Exploits
Last but not least: exploits. Exploits are tools designed to break into systems with security vulnerabilities. If the vulnerability is not public yet, its exploit is called zero-day or 0-day. These are especially dangerous as it’s tough to protect from.
How do we avoid exploits? Update all your software regularly: operating system, software, apps, extensions, and especially your internet browser. If you are being targeted, you should be especially careful and not even click suspicious links or open PDFs on your laptop or mobile phone. Receiving an image on iMessage can infect your mobile device without even clicking on it. These exploits are called zero-click exploits, as they require no action from the victim to infect the device. If you need greater security, you can activate Lockdown mode on your Macbook, iPhone, or iPad.
For Better Security: HD, Multi-Sig and AA
As we’ve observed, asymmetric cryptography is robust, and Web3 can technically depend on it. However, it places a significant responsibility on the holder of the private keys. Imagine if every time someone lost their key, they also lost all their assets and digital identity. It would be catastrophic, wouldn’t it?
This security model poses challenges for global Web3 scalability and mass user adoption. That’s why there are more sophisticated methods to store crypto assets without relying solely on a single private key. Let’s briefly explore these alternatives:
Hardware wallets
HD wallets consist of small physical, electronic devices that create and store our private key internally so that it never leaves the device, making it far more secure than hot wallets, which store keys in devices connected to the internet.
When we need to sign a transaction, the signature is generated inside the secure device, and then the signed transaction is sent to our computer. This way, even if our computer is compromised, the attacker will only be able to see the signed transaction but never access the private key itself. The most well-known hardware wallet brands are Ledger, Trezor, and Safepal.
Multisig Wallets
They are wallets that rely on multiple signers to sign a transaction. For example, we can have a 3/5 multi-signature wallet, which means that we have five different signers (each one with a different private key) and that we need any three of them to sign in order for a transaction to be successfully approved.
This provides both high security and high availability, as in the case that one or two of the signers lose their private keys, the other ones will be able to move the assets anyway. The most know multisigs are Safe (ex Gnosis safe) and Avocado.
Account Abstraction (AA)
AA is a concept primarily discussed in the context of Ethereum. At its core, account abstraction aims to simplify the distinction between user accounts and smart contract accounts, towards a more unified and flexible account system.
For end users, this translates to enhanced privacy, security, and customization features. One notable advantage is the ability for users to define multiple signers for their accounts, adding an extra layer of protection.
Furthermore, users can configure timelocks on their transactions. A timelock ensures that a transaction, once initiated, will only be executed after a specified period, giving users a window to review or cancel if necessary. These features not only bolster security but also provide users with a more tailored experience, granting them greater control and flexibility over their interactions with the Ethereum network.
Conclusion
As we have seen, attackers have many ways and resources to try to steal private keys, as they are getting more sophisticated daily. Hence, it’s essential to apply the above-mentioned security measures.
Always stay informed and updated regarding blockchain security. You can follow us both on our Twitter and Telegram accounts. We are here to help and to make the ecosystem a more secure place.