In the evolving landscape of cybersecurity, zero-knowledge proofs (ZKPs) have emerged as a revolutionary concept, offering a way to prove the veracity of a statement without revealing any information beyond the statement’s validity. This article delves into the intricate world of zero-knowledge proofs, exploring their origins, workings, types, and practical applications in today’s digital environment.
1. What is a Zero Knowledge Proof? Origins and Inventors
A zero-knowledge proof is a cryptographic method that enables one party, the prover, to demonstrate the truth of a statement to another party, the verifier, without conveying any additional information apart from the fact that the statement is indeed true.
Just think for a second. In everyday life, we encounter situations where we have to sign up for a new service or application, and private information is asked for. We have no choice but to hand out our data for access. Something that seemed inevitable until Zero Knowledge Proofs.
This concept was first introduced in the 1980s by three researchers: Shafi Goldwasser, Silvio Micali, and Charles Rackoff. Their groundbreaking work laid the foundation for a new era in cryptographic protocols, focusing on privacy and security.
You can read the original paper here:
The Knowledge complexity of interactive proof systems – Shafi Goldwasser, Silvio Micali, and Charles Rackoff
2. Didactical Example of Zero Knowledge Proof
There are a few didactical examples to explain the concept of zero-knowledge proof and how can be achieved in a non-technological environment. Let’s see the first one:
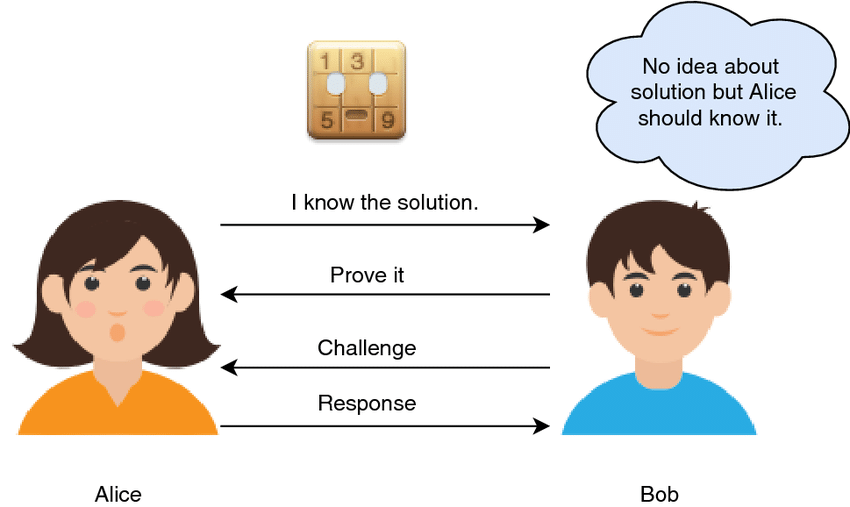
Imagine Alice wants to prove to Bob that she knows the password to a vault without revealing the password itself. They agree on a method where Alice enters the vault, and Bob waits outside. The vault has two doors, A and B. Bob cannot see which door Alice enters, but once she’s inside, he asks her to exit from either door A or B. If Alice truly knows the password, she can open the vault from the inside and exit from the door Bob requests, proving she knows the password without revealing it. This is a simplified analogy for a zero-knowledge proof.
Now let’s see a more complex situation with the same actors and understand the different steps involved in the process and how conditions of Zero Knowledge Proofs are fulfilled.
Scenario Setup:
Bob: Wants to verify Alice’s claim without learning the secret.
Alice: Has a secret to prove to Bob.
The Secret: Alice claims she can distinguish between two balls that appear identical to everyone else but are, in fact, of different colors. Let’s say one is red and the other is blue, but they appear identical to everyone except Alice.
The Zero-Knowledge Proof Process
Step 1 (Preparation): Bob gives Alice the two balls, which appear identical to him. He verifies they are the only objects used in this demonstration.
Step 2 (Challenge): Bob takes the balls behind his back, and either switches them or leaves them in the same hands. He then presents them to Alice again.
Step 3 (Proof without Revelation): Alice, who can supposedly see the color difference, tells Bob whether or not he switched the balls. Remember, to Bob and any onlooker, the balls are indistinguishable.
Step 4 (Verification): Bob repeats this process multiple times. If Alice truly can distinguish the colors, she will be correct every time. If she were guessing, the probability of her being correct every time would become increasingly small with each iteration.
The Result
Verification without knowledge: Bob becomes convinced that Alice can indeed differentiate between the balls, but he gains no knowledge about what the difference is (in this case, the colors).
Repeatable and consistent: The process can be repeated many times to reduce the chance of Alice simply being lucky with her guesses.
No additional information leakage: At no point does Alice reveal any information about the nature of the difference between the balls. Bob only learns that there is a difference and that Alice can detect it.
However real-world cryptographic applications are far more complex and mathematical. However, the core idea remains the same: proving the validity of a statement without revealing any additional information beyond the validity of that statement. In cryptographic terms, this is often about proving the possession of specific knowledge (like a password or a cryptographic key) without revealing the knowledge itself.
3. How Do Zero Knowledge Proofs Work? Technical Perspective
Technically, zero-knowledge proofs involve complex algorithms and cryptographic techniques. They are based on mathematical constructs where the prover can generate a proof (a set of cryptographic data) that can be verified by the verifier. This proof does not contain any information about the actual data or statement, just the assurance of its truthfulness. Advanced mathematical principles like computational hardness assumptions play a crucial role in ensuring the security and reliability of these proofs.
A simplified explanation of the cryptographic foundations of ZKPs
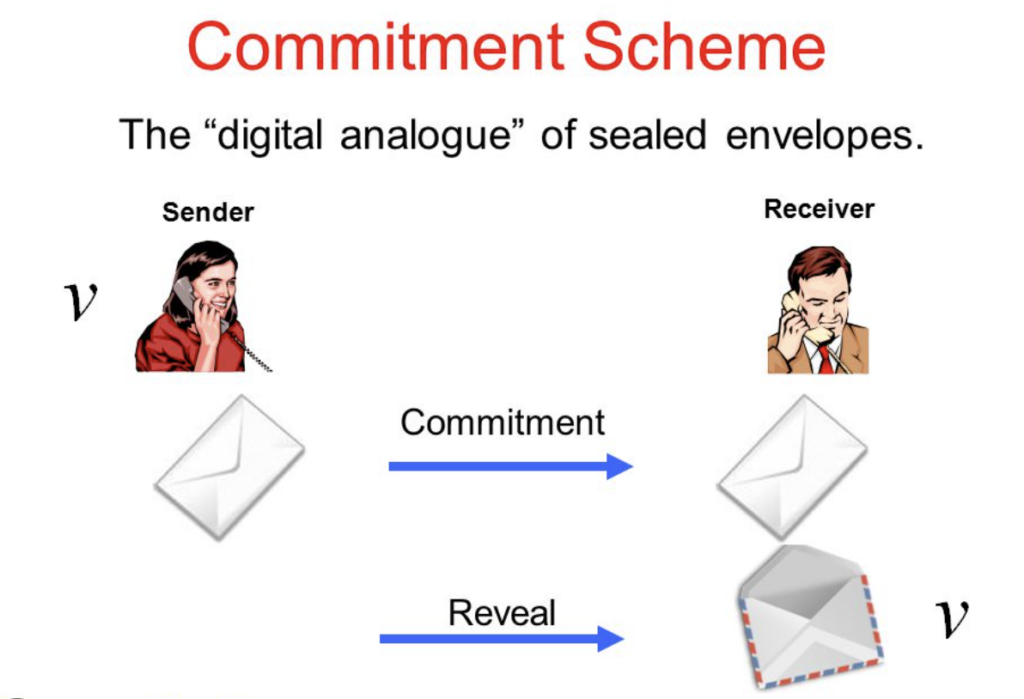
1. Digital “Sealed Envelopes” (Cryptographic Commitments)
Think of ZKPs as involving something similar to a digital version of a sealed envelope. In real life, you can put a secret note in an envelope and seal it. The note is hidden, but you know it’s there, and you can choose to show it later. In ZKPs, we use a digital version of this, where a person (the prover) can commit to certain information (like a secret number) without showing what it is. Later, they can reveal it to prove that they were honest about what they committed to.
2. Unique Digital Fingerprints (Hash Functions)
Just as our fingerprints are unique to us, there are functions in cryptography that can take any piece of data and produce a unique digital fingerprint of it. These are called hash functions. They are crucial in ZKPs, especially in the versions where you don’t need continuous back-and-forth communication (non-interactive). These digital fingerprints help create challenges and checks within the proof process, making sure everything is secure and tamper-proof.
Mathematical Constructs in ZKPs – Simplified
1. Interactive Conversation (Interactive Proofs)
In the original form of ZKPs, the process is like a conversation where one person (the prover) keeps convincing the other (the verifier) through a series of steps. The verifier asks questions (challenges), and the prover provides answers (evidence) without revealing the secret.
2. Solving Tough Puzzles (Hardness Assumptions)
The security and reliability of ZKPs are based on really tough mathematical puzzles. Just like a complex jigsaw puzzle is hard to put together but easy to see if it’s right once done, these cryptographic puzzles are extremely hard to solve but easy to verify once a solution is found. These tough problems are the bedrock of making ZKPs secure.
3. Complex Problems, Easy Verification (NP Problems)
In the world of computer science, ZKPs are particularly useful for a type of problem where finding a solution is hard (like solving a complex riddle), but if someone tells you a solution, it’s quite easy to check if it’s correct.
In simpler terms, zero-knowledge proofs are a way to say “I know a secret, and I can prove I know it without telling you what it is.” They use digital versions of sealed envelopes and unique fingerprints to do this securely. It’s like proving you have the key to a treasure chest without showing the key itself. This concept, although grounded in complex cryptography and mathematics, opens up exciting possibilities for enhancing privacy and security in our increasingly digital world.
4. Types of Zero Knowledge Proofs
Let’s delve into the different types of zero-knowledge proofs (ZKPs), which vary based on their structure, interaction model, and specific use cases. Understanding these variations is crucial in appreciating the broad applicability and flexibility of ZKPs in various technological domains.
1. Interactive Zero-Knowledge Proofs (IZKPs)
Description: In IZKPs, the prover and verifier engage in a direct, iterative conversation. The verifier presents a challenge, and the prover responds with proof, with multiple rounds of interaction to establish trust.
Example: The classic example is the “Where’s Waldo?” puzzle. Imagine the prover claims to know Waldo’s location in a large picture. The verifier covers the entire picture except for a tiny window, which can be moved around. If the prover consistently points out Waldo through this window across many iterations, the verifier is convinced without learning Waldo’s exact location.
2. Non-Interactive Zero-Knowledge Proofs (NIZKPs)
Description: NIZKPs eliminate the need for multiple interactions. The prover can generate a proof independently, which the verifier can check at their convenience.
Example: Consider a digital signature. The prover signs a document using a private key (the secret), generating a signature (the proof). Anyone with the public key (the verifier) can verify the signature’s authenticity without interacting with the signer or learning the private key.
3. Zero-Knowledge Proofs of Knowledge
Description: These focus on proving the possession of specific knowledge without revealing the knowledge itself.
Example: In a password authentication scenario, the prover can prove knowledge of the password without actually transmitting the password. This is often implemented using cryptographic techniques like hash functions.
4. Succinct Non-Interactive Zero-Knowledge Proofs (zk-SNARKs)
Description: zk-SNARKs are a subset of NIZKPs that are both succinct (requiring minimal data) and non-interactive. They are especially useful in blockchain technologies.
Example: In a blockchain context, a user can prove that a transaction is valid (complies with all rules and constraints) without revealing any details about the transaction itself.
5. Zero-Knowledge Succinct Transparent ARguments of Knowledge (zk-STARKs)
Description: Similar to zk-SNARKs but with an emphasis on transparency, avoiding the need for a trusted setup (which is a security risk in zk-SNARKs).
Example: zk-STARKs can be used in supply chain management to verify the authenticity and journey of a product without revealing sensitive or proprietary information about the product or the supply chain process.
6. Zero-Knowledge Contingent Payments (ZKCP)
Description: This is a protocol combining ZKPs with smart contracts to facilitate transactions contingent on the proof of knowledge.
Example: In a digital marketplace, a seller can prove the possession of a rare digital item without revealing it. Upon proof verification, a smart contract ensures the automatic transfer of payment and items between buyer and seller.
Conclusion
These different types of zero-knowledge proofs cater to various requirements in terms of interaction, data efficiency, transparency, and specific application contexts. From safeguarding privacy in digital transactions to enabling secure authentication processes, the versatility of ZKPs is a testament to their potential to shape the future of secure and private digital communication.
5. Use Cases of Zero Knowledge Proofs
Zero-knowledge proofs (ZKPs) have a wide range of applications across various industries, leveraging their unique capability to verify the truthfulness of a statement without revealing any additional information. Let’s explore some of these diverse use cases:
1. Blockchain and Cryptocurrency
Privacy-Enhanced Transactions: In cryptocurrencies like Zcash, ZKPs enable transactions where the sender, receiver, and amount are encrypted but still verifiable as valid by the network.
Smart Contracts: ZKPs can enhance the privacy and security of smart contracts by allowing certain conditions to be verified without exposing underlying data.
2. Financial Services
KYC (Know Your Customer) and AML (Anti-Money Laundering): ZKPs allow for the verification of client information for regulatory compliance without banks and financial institutions needing to exchange or reveal actual sensitive data.
Credit Scoring: Individuals can prove they have a good credit score to lenders without revealing their exact credit score or detailed financial history.
3. Identity Verification
Authentication Systems: ZKPs can enable users to authenticate to services (like logging into websites) by proving they know the password without actually transmitting the password.
Privacy-Preserving Identity Checks: Users can prove attributes (age, nationality, etc.) without revealing other personal information or the documents themselves.
4. Healthcare
Confidential Health Records: Patients can prove they meet treatment criteria or have certain health conditions without revealing their entire health history.
Pharmaceutical Supply Chains: ZKPs can be used to verify the authenticity and proper handling of pharmaceuticals throughout the supply chain without exposing sensitive business information.
5. Online Voting Systems
Voter Anonymity and Vote Integrity: ZKPs can allow voters to prove that their vote was cast correctly without revealing who or what they voted for, thereby maintaining the integrity and secrecy of the vote.
6. Supply Chain Management
Product Authenticity: Companies can prove the authenticity and origin of their products (like organic or fair-trade certification) without revealing sensitive supply chain details.
Regulatory Compliance: Businesses can prove compliance with regulatory requirements without disclosing proprietary or competitive information.
7. Intellectual Property and DRM (Digital Rights Management)
Proof of Ownership: Creators can prove they own a digital asset (like artwork, music, or software) without revealing the asset itself.
Access Control to Digital Media: ZKPs can enable users to access digital media content they have rights to without exposing their identity or the specifics of their rights.
8. Education and Employment
Credential Verification: Individuals can prove they possess certain academic or professional qualifications without revealing the specific details or documents of those qualifications.
Background Checks: Job candidates can verify aspects of their background to potential employers without disclosing personal information.
Conclusion
The versatility of zero-knowledge proofs in enhancing privacy, security, and efficiency is evident across these varied industries. From safeguarding sensitive financial data to ensuring the integrity of online voting systems, ZKPs offer a powerful tool to maintain confidentiality while ensuring the reliability and veracity of critical data and transactions. As technological advancements continue, the potential applications of ZKPs are expected to grow, further embedding them in the fabric of digital interaction and exchange.