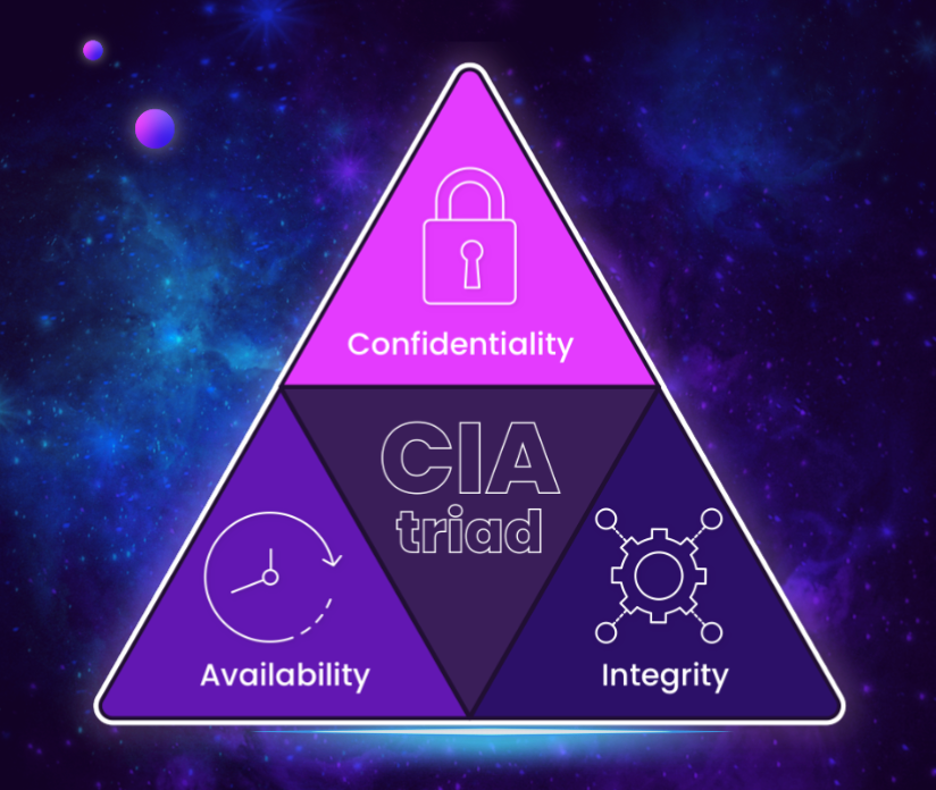
The CIA triad, also known as the AIC triad in cybersecurity, is an acronym that stands for what are considered the three fundamental components of security: Confidentiality, Integrity, and Availability. It is an organizational model widely adopted to guide security measures, controls, and overall strategy to protect information within organizations. Each component of the CIA triad plays a critical role in ensuring that information systems are secure and reliable.
Confidentiality
Confidentiality involves protecting information from unauthorized access and disclosure. The data should be accessible only to those we want to have access. In the context of enterprise security, a breach of confidentiality can occur when unauthorized individuals view, steal, or modify sensitive data. Confidentiality is achieved through two main technologies: Access Controls and Encryption.
- Access Controls: This confidentiality component can also be divided into two steps: authentication and authorization. Authentication is related to your identity and who you are; in this part, secure password setups and two-factor authentication methods are fundamental. On the other hand, authorization is related to the permission or allowance to do something. A role-based model can allow an authenticated user to access particular privileges according to a given role or category of permission.
- Encryption: Information must flow in an organization; authorized users will need to communicate between them, and to ensure confidentiality, it is necessary to rely on secure channels that make it impossible for unauthorized users to intercept the message and access it. Encryption enables the communication and the safe travel of information in a way that only users with a key can decipher the message.
Integrity
Integrity ensures that data and systems are consistent, accurate, and have not been tampered with or altered by unauthorized parties. It’s about maintaining the correctness of data and the trustworthiness of systems. Techniques to uphold integrity include the use of checksums, hashing, version controls, and access controls that prevent unauthorized data modification. Integrity is crucial for ensuring that the data an organization relies on for decision-making, operations, and reporting is accurate and dependable.
Availability
Last but not least, availability ensures that data, systems, and services are accessible to authorized users when needed. This involves keeping systems up and running, even in the face of attacks or failures. Measures to support availability include redundancy, fault tolerance, load balancing, and DDoS mitigation strategies. Availability attacks, like ransomware, can limit access to vital information systems, severely impacting an organization’s operations.
Growing Challenges To Achieve CIA
Navigating the complexities of the CIA (Confidentiality, Integrity, Availability) triad presents multifaceted challenges within the contemporary digital landscape. These challenges are exacerbated by several pivotal factors:
The exponential growth of data: The advent of big data introduces formidable obstacles for the CIA framework, attributed to the overwhelming volumes of data that need to be safeguarded. This issue is compounded by the diverse origins of this data, alongside the myriad of formats it assumes. The proliferation of duplicate data sets and the imperative for Disaster Recovery (DR) strategies further inflate the already substantial costs associated with data protection.
Governance and data stewardship: The primary focus within the big data realm on accumulation and the extraction of actionable insights often results in a deficiency in responsible data stewardship, auditing, and governance. This gap in oversight was starkly highlighted by whistleblower Edward Snowden’s revelations concerning the National Security Agency’s extensive collection of personal data belonging to U.S. citizens, spotlighting significant privacy concerns.
Internet of Things (IoT): The IoT ecosystem, characterized by its ability to endow a vast array of physical and logical entities with unique identifiers and autonomous communication capabilities, poses unique security and privacy challenges. While data transmitted by individual IoT endpoints may seem innocuous in isolation, the aggregation and analysis of fragmented data from multiple sources can unveil sensitive information. The security conundrum is further complicated by the extensive array of internet-enabled devices, often left unpatched or secured with default or weak passwords, transforming IoT into a potential vector for cyber-attacks or a component of a broader malicious network.
Product development security: The integration of networking capabilities into a widening array of products necessitates a preemptive and continuous focus on security throughout the product development cycle. As the availability of network-connected products escalates, so too does the spectrum of potential vectors through which cyber adversaries may seek to infiltrate and extract sensitive data.
Today, we are not only grappling with the colossal volumes of data generated every second but also navigating through a myriad of new devices and products that were not architected with security as a cornerstone or in alignment with the foundational principles of the CIA model. This proliferation of technology, ranging from Internet of Things (IoT) devices to cloud-based services and beyond, introduces unprecedented challenges in safeguarding information. Many of these modern innovations were designed and deployed with the primary focus on functionality, convenience, and speed to market, often sidelining the critical aspects of data security and privacy. As a result, these devices become fertile ground for vulnerabilities, exposing personal and corporate data to potential breaches and attacks.
Addressing these challenges demands a nuanced understanding of the evolving digital ecosystem and a commitment to adopt advanced security measures, governance practices, and a proactive stance on privacy and security from the inception phase of product development. The goal has to be ensuring that every new device or product is developed with a keen perspective on adhering to the CIA triad, thus fortifying our digital ecosystem against the ever-evolving cyber threats.
CIA Model Best Weapons: Evolving Technologies
Despite everything, technology also advances in a way that can allow us to solve the problems mentioned above. Let’s see some of them:
Cryptography
This technology is achieved through complex mathematical transformations, rendering data unreadable to unauthorized users. There are several kinds of cryptography:
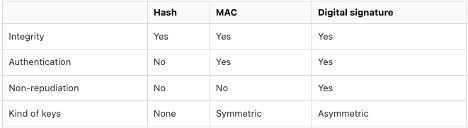
An unkeyed hash function, when appended to a message, primarily serves the purpose of ensuring data integrity. It allows the detection of accidental alterations to the message or the hash. However, since it doesn’t involve encryption keys, an attacker could modify the message and generate a new, matching hash, thus bypassing this integrity check. The integrity protection is enhanced when the hash is sent through a secured channel, separate from the message, making it harder for attackers to tamper with the message unnoticed.
Message Authentication Codes (MACs), or keyed hashes, add a layer of security by incorporating a secret key into the hash function. This mechanism ensures that only parties with access to the shared secret key can authenticate the integrity and origin of the message, providing both data integrity and authentication. However, MACs do not offer non-repudiation since the sender could deny the message’s creation, and they are susceptible to replay attacks unless additional measures, like timestamps or sequence numbers, are implemented.
Digital signatures, leveraging asymmetric cryptography, use a private key for signing a message and a public key for verification. This setup guarantees the message’s integrity, authenticates the sender’s identity (since only the holder of the private key could have signed the message), and provides non-repudiation, preventing the sender from denying the act of signing. Digital signatures, however, do not inherently prevent replay attacks and are generally more computationally intensive than MACs, making them less suitable for scenarios requiring fast or frequent message exchanges.
Blockchain Technology
Integrity in cybersecurity ensures that information remains unaltered and trustworthy from its source to its destination. Blockchain technology, originally devised for digital currencies like Bitcoin, has emerged as a powerful ally in maintaining data integrity. Blockchain is a decentralized and distributed ledger that records transactions across many computers so that any registered transaction can be verified and audited, but not altered retroactively.
Blockchain’s application extends beyond cryptocurrencies, securing the integrity of a wide array of digital transactions and information exchanges. Each block in the chain contains a cryptographic hash of the previous block, creating an unbreakable chain of trust. This makes blockchain an ideal technology for scenarios where data integrity is paramount, such as in supply chain management, secure voting systems, and the verification of digital identities. The technology acts as a digital seal, ensuring that once information is recorded, its authenticity and accuracy remain intact, free from tampering or corruption.
Blockchain technology also achieves availability through its inherent design, which incorporates fault tolerance protocols. Fault tolerance in blockchain is primarily achieved through decentralization and consensus mechanisms. Unlike centralized systems, where a single point of failure can disrupt service, blockchain distributes its operations across a network of computers (nodes). This means that even if some nodes fail or are compromised, the blockchain continues to function without any loss of service, ensuring high availability.
Blockchain uses consensus models like Proof of Work (PoW), Proof of Stake (PoS), and others to ensure that all transactions and data are verified and agreed upon by multiple nodes. This not only secures the network but also ensures that as long as a majority of nodes are operational, the blockchain remains functional and available. In the event of a node failure, the consensus mechanism allows the network to automatically reorganize and validate pending transactions with the remaining active nodes.
Redundancy
It is a technique that refers to duplicating critical components or functions within a system to increase reliability and availability. The main goal of redundancy is to ensure that a system can continue to operate in the event of a failure or a fault in one part of the system. This concept is pivotal for maintaining high availability and preventing data loss or service interruptions. There are several methods and strategies involved in implementing redundancy, like hardware redundancy, software redundancy, data redundancy, network or geographical redundancy.
Each of these methods contributes to building a resilient infrastructure that can withstand various failure modes, ensuring that critical systems and data remain accessible when needed. Implementing redundancy is a fundamental aspect of designing robust IT systems, particularly for applications and services where high availability is a critical requirement.
Cloud Computing
Cloud computing is a relatively new technology that delivers a range of computing services—such as servers, storage, databases, networking, software, analytics, and intelligence—over the Internet (“the cloud”) to offer faster innovation, flexible resources, and economies of scale. Users typically pay only for the cloud services they use, helping them lower their operating costs, run their infrastructure more efficiently, and scale as their business needs change. Cloud computing plays a significant role in enhancing each aspect of the triad:
- Confidentiality: Cloud service providers implement stringent security measures to protect data confidentiality. This includes data encryption, both at rest and in transit, ensuring that sensitive information is inaccessible to unauthorized users. Advanced encryption techniques and identity and access management (IAM) systems are employed to control who has access to information based on their roles and responsibilities.
- Integrity: Cloud platforms offer services that ensure data integrity by protecting it from unauthorized changes and ensuring its accuracy and consistency over its entire lifecycle. This is achieved through various mechanisms such as checksums, versioning, and transaction logs that record every operation on the data. Additionally, data integrity is maintained during transfers with secure protocols and storage with integrity verification tools.
- Availability: One of cloud computing’s strongest advantages is its ability to provide high availability and disaster recovery solutions without the need for extensive physical infrastructure. Cloud providers deploy data across multiple geographically dispersed data centers, ensuring that services can be maintained even in the event of a disaster or failure in one location. Scalability features allow resources to be dynamically allocated based on demand, ensuring that applications remain available to users without interruption.
The cloud’s flexible and scalable nature allows organizations to adjust their resources to meet their security needs, enhancing their ability to protect against and respond to cybersecurity threats. By leveraging cloud computing, businesses can effectively address the challenges posed by the CIA triad, ensuring that their data is secure, intact, and available whenever needed.
Trade-offs: Is it Possible to Achieve a Balance?
As Thomas Sowell once said, “There are no solutions, only trade-offs.”
Confidentiality vs. Availability: Increasing confidentiality measures, such as multi-factor authentication and encryption, can sometimes impede the availability of data. For instance, rigorous access controls may delay authorized users’ access to information when needed promptly.
Integrity vs. Availability: Implementing stringent integrity checks, like cryptographic hash functions and digital signatures, ensures data authenticity but might impact system performance, affecting availability. These checks require processing power and time, potentially slowing down system access.
Confidentiality vs. Integrity: In certain cases, mechanisms that protect data integrity, such as open auditing logs, might pose challenges to confidentiality by revealing sensitive information to ensure data has not been tampered with.
Achieving Balance
To start, every organization should conduct regular risk assessments to identify their most valuable assets and the most relevant threats to these assets. This process helps prioritize which of the CIA triad components need more focus, based on the likelihood and impact of potential threats.
In the pursuit to achieve a perfect balance among confidentiality, integrity, and availability, organizations must understand that there is no single measure that can ensure total security; instead, employing a layered (or defense-in-depth) security strategy that addresses all three components of the CIA triad is the wisest choice. The utility of this model resides in understanding and assessing organizational risks, prioritizing protection based on the severity of consequences should any component of the triad be breached. Also, developing flexible security policies that can be quickly adapted to changing threats and business needs is essential. This includes having clear procedures for access control, data encryption, and incident response. Furthermore, organizations must continuously monitor their security posture and adapt their strategies based on new threats, technological advancements, and lessons learned from security incidents.
In conclusion, there is no one-size-fits-all approach to perfectly balancing the components of the CIA triad. Each organization must evaluate its specific needs, the sensitivity of its data, and its operational requirements to develop a tailored strategy that effectively balances confidentiality, integrity, and availability. By understanding the trade-offs and employing a strategic approach to security, organizations can safeguard their assets while ensuring their systems and data remain accessible and reliable to support business operations. The CIA triad must serve as a foundational model in cybersecurity, guiding organizations in protecting their information assets. By carefully balancing confidentiality, integrity, and availability, organizations can develop a robust security posture that defends against a wide range of threats while ensuring that their systems remain usable and reliable.